- Automated and manual vulnerability management capabilities and processes that adhere to risk assessment results (500.5(a)(2))
- Privileged access management and password management capabilities and processes prioritizing password security and system access control (500.7)
- Risk-focused capabilities (both preventive and detective) and processes enhancing password security and system access control (500.14(a)(2))
- Endpoint detection and response, and centralized logging and security event alerting capabilities and processes to enable monitoring of critical events (500.14(b))
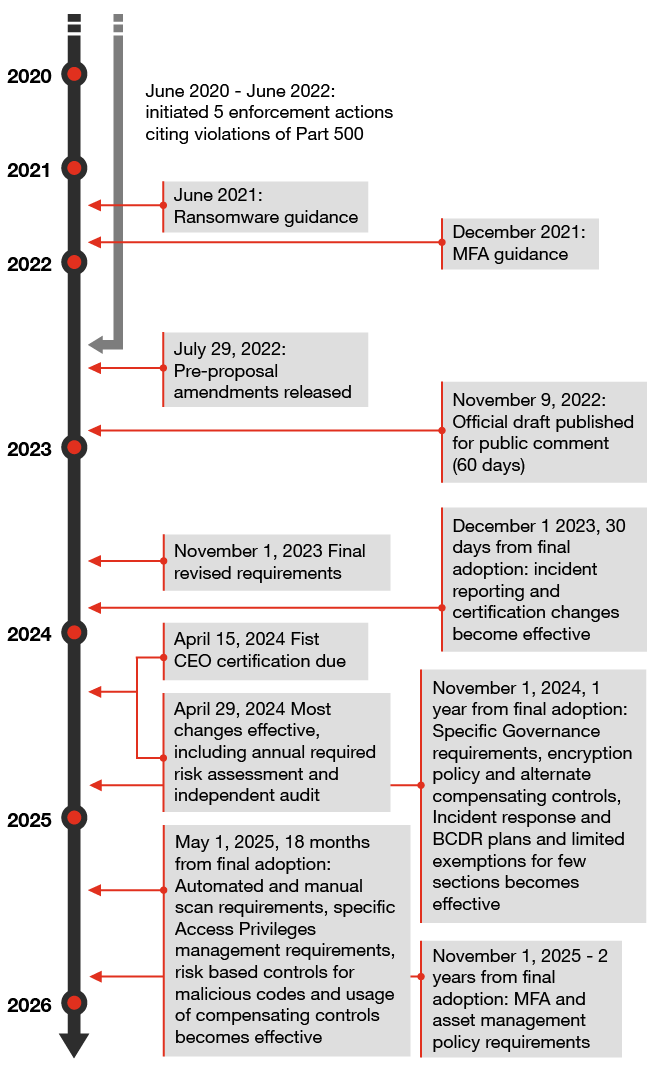
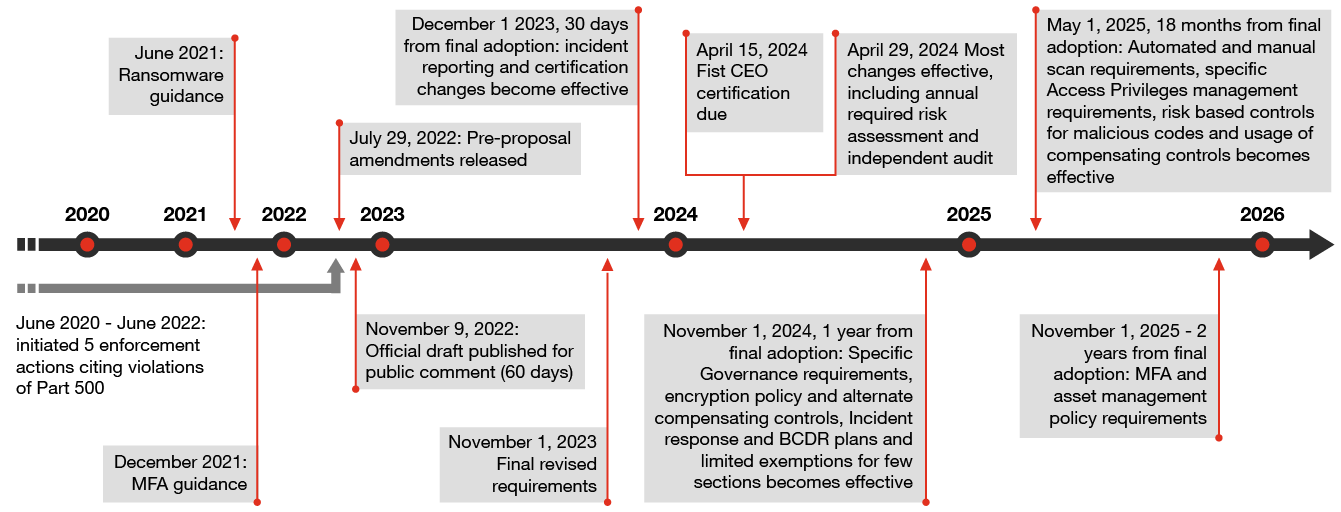
The newly effective version requires the ability to certify for “material” compliance. The regulator has left it up to each covered entity to define and establish criteria for material compliance, previously noting that materiality will vary for each covered entity and will depend on their specific circumstances. Material compliance is also referenced within 500.20(b) in communicating criteria for citing violations that can lead to fines and other penalties.
What you need to do
The waiting is over. Now’s the time to take action.
- Define “material.” Because the regulation now requires material compliance, and several sections refer to materiality thresholds, it’s essential to establish well-documented criteria for assessing materiality. It’s important to note, materiality will apply at the level of the covered entity, and if there are multiple covered entities as part of a larger group structure, what’s material for one may not be material for another. Also, what’s material for a covered entity may or may not be material from an enterprise perspective, or at the level of an SEC registrant. Clearly documenting criteria and decision making will facilitate the evaluation and documentation of compliance, especially when examiners raise questions.
- Enhance cybersecurity incident notification and related follow-up processes. Communications supporting material cybersecurity incidents within the organization, its affiliates or third-party service providers to the regulator must support compliance by December 1, 2023 (see 500.17(a) and 500.17(c)). Also see ‘Navigate competing SEC disclosure obligations’ below.
- Enhance compliance evidence for CEO sign-off. This change is effective for the 2023 certification, due for submission by April 15, 2024 (see 500.17(b)). The requirement that the CEO cosign with the CISO and that certification be based on data and documentation sufficient to demonstrate “material” compliance will require a move away from control owner attestation and toward collecting evidence of control execution and effectiveness. Some firms may be able to present a single package of documentation demonstrating how each requirement is met, with mapping to policies, procedures, controls and control execution or testing evidence. Others should identify this as their target state. Because firms must certify based on this evidence, gaps in the ability to do so may now open those who can’t to regulatory sanction, fines and other penalties.
- Identify areas that require immediate attention. The process of conducting a full inventory of assets to meet the updated requirements may be time-consuming, yet this inventory is indispensable for shaping the risk assessment underpinning your entire cybersecurity program. For many organizations, creating and maintaining a thorough asset inventory can present significant challenges, making it the likely bottleneck despite the two-year window for completion.
- Identify stakeholders, critical paths and necessary staging. Stakeholders encompass staff, senior management, the board, and customers who may be impacted by the heightened security requirements for accessing their accounts. Some changes may be straightforward, such as administrative adjustments to incident-reporting protocols, while others — like endpoint detection for Class A companies, the asset inventory, and BCDR testing — will necessitate broader involvement from stakeholders across the organization. With certification now including domains outside the typical CISO responsibility, such as asset inventories and continuity testing, an independent audit that includes them will be important in supporting both CISO and CEO certification. It will be necessary to align CISO, technology and resiliency organizations with independent audit around capability requirements, control design and execution expectations and what constitutes evidence sufficient to support certification.
- Budget for the changes. With corporate budgeting for the coming year firmly underway, firms should begin planning for any necessary technology improvements. The two years to meet the asset inventory and MFA requirements will pass quickly, and the NYSDFS has shown that it’s an aggressive enforcer. For larger firms, start analyzing whether the Class A designation applies. All firms should set aside resources for compliance planning and preparations in this budgeting cycle. For example, the elimination of text messages as a permissible component of an MFA solution and the requirement that the CISO review and approve at least annually in writing any compensating controls may require enhancing your MFA approach and related technologies. Applying and periodically reviewing the principle of least privilege and privilege account management may be a heavy lift, depending on your firm’s size and complexity.
- Assess your current pace of testing, control execution, control testing and evidence collection. It may be necessary to expedite testing processes to meet deadlines, alongside the implementation of readiness and business continuity plans. Confirming you have the right talent in all three lines of defense is crucial, particularly in the context of a competitive and challenging job market. Comprehensive documentation of control execution evidence, as well as evidence from second- and third-line (i.e., independent) testing, is indispensable to support the annual certification process.
- Confront your technology debt before it comes due. For some covered entities, the required changes may prompt discussions around broader technology uplift. The asset management policy must be enhanced to speak to end-of-life management by April 29, 2024; encryption must be expanded by November 1, 2024; and MFA expanded and the asset inventory completed by November 1, 2025. At this point, it may become apparent that certain legacy assets, which may be beyond end of support life, are incapable of supporting encryption or MFA — in contrast to what the asset management policy requires. Add in the independent audit requirement, which may well examine one of more of these program elements, and organizations that have put off upgrades may find themselves confronting that deferred technology investment.
- Navigate competing SEC disclosure obligations. For publicly listed financial services firms subject to the SEC’s recent cybersecurity disclosure rule published in July and effective as of September, the NYDFS requirements may pose coordination challenges. Both require incident reporting, but the scope and materiality definitions may differ. For example, the NYSDFS rule applies to the covered entity, which may be one of several subsidiaries of a parent company subject to the SEC rule. However, there are also synergies, such as the mutual emphasis on board oversight, raising the stakes for board members to increase their education around the cybersecurity threat environment in order to effectively challenge management.